Spotting Fake News: Behavior Design for Cyber Security Training
You open your personal email account and see an email that looks like it’s from your bank: TrustedBank. This is an email you would normally respond to, but having gone through a few weeks of cybersecurity training around reporting phishing scams...you know something smells fishy.
You identify it as a scam and report it. Then you actually call your cybersecurity provider to thank him for the training. This series of events actually happens on a regular basis to Kreitzberg.
Doug Kreitzberg is a graduate of BJ Fogg’s 2-Day Behavior Design Bootcamp. After completing the training in 2018, he was inspired to apply Behavior Design to his business, Designed Privacy, a provider of digital security and data privacy solutions for small and medium-sized businesses. His primary goal was to test and refine a new way to reduce employee vulnerability to phishing scams that demonstrated behavior change over time. Fogg recommended that Kreitzberg work with David Ngo, the Behavior Designer in-Residence at the Peace Innovation Lab, to achieve this outcome using the process of Behavior Design and SnapTesting (a specific Behavior Design method).
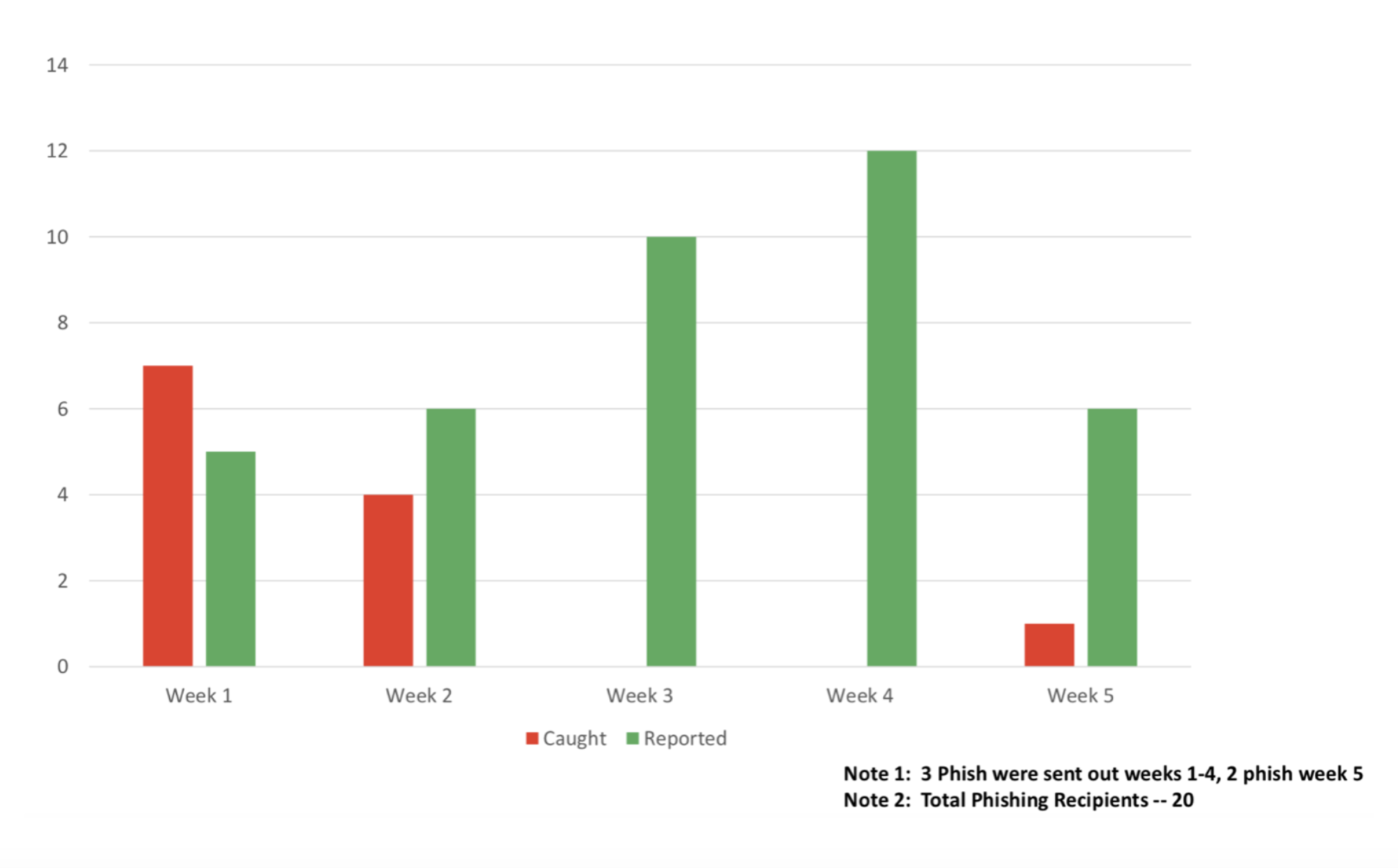
After four months of SnapTesting on various companies, Kreitzberg and Ngo experienced their first breakthrough success, as seen above: they were able to increase phish detection in employees by 68% and decrease employees clicking security compromising links to 0% within four weeks. Ngo called a meeting with Margarita Quihuis to explore the potential for PeaceTech in this new behavior designed intervention. Here was her response:
“Enterprise could be the first line of defense for positive information (and training). Can this training spill over to the personal sphere? Can this bring people together and connect with one another (pro-social behaviors)? – Margarita Quihuis, co-director of the Stanford Peace Innovation Lab
Kreitzberg and Ngo realized that they were unknowingly sitting on a tool that could be used as PeaceTech. So, for another four months they added an additional Peace focus to their Behavior Design project: to increase social connection among employees, families, and communities.
Before diving deeper, let’s take a step back and provide more context. When Kreitzberg and Ngo began working together, they asked themselves three guiding questions:
Can we develop a cost-saving data security solution applying Behavior Design?
Can we change the behaviors of vulnerable employees?
Can we SnapTest our way to a new Behavior Design driven product to achieve two primary outcomes:
Reduce unwanted outcomes; employees stop clicking on security-compromising links
Increase desired outcomes; employees know the difference between a phishing scam and a real email
Furthermore, Kreitzberg introduced this new intervention to employees with four guiding principles:
Respect for the test subject (i.e. you);
Simplicity and Ease of Use;
Make it engaging (if not fun);
Focus on enhancing digital mindfulness, a skill we all need going forward.
Kreitzberg and Ngo returned to the Behavior Design process and SnapTesting over and over again for the next four months after the first breakthrough. The results remained consistent. There was a continued increase in wanted behaviors (employees reporting phishing scams). Especially meaningful is that those who were phished actually began identifying and reporting scams (from 25% to 100% in two weeks). Testing of mid-size insurance company was done in July / August, 2019.
As more business and behavior metrics were achieved, the connection to PeaceTech became clearer, too. The new Behavior Design Driven program decreased unwanted behavior (employees click on security compromising links) and increased wanted behaviors (employees reporting phishing scams – especially if they had been phished in the past as seen in the graph above). More than anything, it prompted pro-social behaviors, aka bringing people together.
Here are the metrics of the latest Behavior Design Driven Cybersecurity campaign that Kreitzberg and Ngo conducted with a mid-size insurance company in July / August, 2019.
36% said "I have talked about phishing techniques with my family."
36% said "I have talked about phishing techniques with my co-workers."
48% said, "I would recommend this type of program to my vendors, clients, community (school/church/etc)."
70% said, "I would recommend we do a program like this periodically."
The unexpected, interesting insight in the data here is that all employees that talked about phishing techniques with their co-workers ALSO talked to their family; or vice versa. In other words, 100% of employees that decided to talk about the phishing techniques — did so both at work AND home. This indicator highlights the PeaceTech potential of this new intervention designed by Kreitzberg and Ngo.
It’s also encouraging that Designed Privacy’s latest version of the Behavior Design driven intervention at the mid-sized insurance firm (above) had 82% of the responders say at the latest end of a four-week program, “I am more discerning with regards to internet sources when it comes to making decisions.”
82% said, “I am more discerning with regards to internet sources when it comes to making decisions.”
Not only did the target behaviors result in behavior change adoption by almost 50% of employees within a short period of time (four weeks), it also brought people together at work, at home, and increased people’s decision-making ability by better discern true/fake information. This real world case study demonstrates a successful behavior design intervention in enterprise cybersecurity and creates an example of PeaceTech that increases prosocial behaviors and discernibility.
The target behaviors resulted in adoption by almost 50% of mid-sized insurance organization within a short period of time (four weeks).
Let’s also take a look at the financial motivation and impact of a security breach for both enterprises and employees.
Economic incentive for enterprises:
The average total cost of a data breach is $3.9Million USD (source: IBM/Ponemon, 2019) and over 33% of breaches included social attacks (source: Verizon, 2019). Note that the average cyber awareness program is around 1% of IT spend (source: MediaPro).
Economic incentive for employees:
There is an inherent economic incentive for employees, as they do not want to be flagged as a “security risk.” Beyond job retention, employees want to protect their personal finances .
What is the economic value and impact from a PeaceTech lens?
If Designed Privacy’s four-week training program is increasing employee ability to spot what’s real/fake both at work and home, frequency of talking with co-workers about phishing techniques, and also sharing it at home, then we can see how it connects to the global problem of fraud.
Monetary damage caused by cyber crime reported to the FBI has grown from $500M in 2011 to 2.7 Trillion Dollars in 2018. (Source: FBI; IC3; US Department of Justice)
31% of worldwide fraud is due to cybercrime (source: PwC)
In this section, you’ll learn about Kreitzberg and Ngo’s high-level testing process and what they did differently compared to other more traditional approaches.
So, how did Kreitzberg and Ngo design and discover an intervention that produced, in a four week period, a 30% reduction in overall phish susceptibility and for individuals who had already been identified as habitual “phish clickers”, a reduction from 35% susceptivity to 0%? The short answer: open mindedness, Behavior Design/ SnapTesting, and enough time (8 months in this case).
A successful phishing breach by hackers starts with an email and a URL.
Imagine you work in a small accounting firm as the administrative assistant. You receive several emails from an email address that appears to belong to a business partner requesting payment for legal services. As the administrative assistant, you are in charge of releasing funds for routine invoices. You comply because of the believability of the email address, the wire addresses at legitimate banks, and a seemingly legitimate invoice. A lapse of discernment of what’s true and what is fake information leads you to click on both the email, URL, and submitting funds. This series of moments would cost the firm nearly $700,000 in one year — about half the firm’s average yearly revenue. You would not be alone in this because this is an actual example with identifying information removed.
This is a common scenario called “Invoice Fraud.”
So what has been the traditional approach to helping you, professionals, respond to these phishing attempts? Here’s how traditional cybersecurity firms respond to these “cyber awareness” problems:
Traditional firms adopt a “Gotcha!” approach (punishment).
After you click on a “fake, simulator” phish in your email inbox, you see that you’ve just been phished and you are instructed to watch an educational video.
Traditional firms focus on the “Information-Action Fallacy” (a Behavior Design concept by Fogg)
This concept presumes that information will lead to action or behavior change.
If information and education alone were enough, everyone would only have healthy, helpful, and happy habits, and professionals wouldn’t click on security-compromising links!
This is why Kreitzberg and Ngo made behavior change the primary focus (vs education). Instead of using the “gotcha!” approach, they emphasized and reinforced positive behaviors (such as reporting phish) and transparency in sharing progress and overall results. By focusing on helping people feel successful, the campaign produced a positive result: a 30% reduction in overall phish susceptibility, and for individuals who had already been identified as habitual “phish clickers”, a reduction from 35% susceptivity to 0%. All in a four week period.
By focusing on helping people feel successful, rather than guilt, Kreitzberg and Ngo achieved behavior change: campaigns ultimately produced, in a four week period, a 30% reduction in overall phish susceptibility and for individuals, who had already been identified as habitual “phish clickers”, a reduction from 35% susceptivity to 0%.
Often times, innovators believe their solutions must be complex for them to work, yet we intuitively know that simplicity changes behavior.Moving away from punishment to help people feel successful may seem like a small action, but it is not. The Behavior Design driven cyber security training program outlined in this article has helped employees possess a greater scrutiny over online sources, which has led to impact areas far beyond cyber security risk reduction. It’s made a real difference in people’s financial lives at home (like the opening scenario) as well as increased the number of reported real phishing attacks, ultimately protecting the organizations that were part of these campaigns.
Punishment tells people what not to do, but doesn't bolster people with what to do.
Helping people feel successful for doing the target behavior leads to more effective and joyful change in people.
Based on early results, this Behavior Design driven cyber security training program has helped employees possess a greater scrutiny over online sources which has the potential to be impactful in areas beyond cyber security risk reduction. Imagine the cybersecurity attacks happening not to businesses, but to every day people: young and senior folks; women and men; all ethnicities, socio-economic backgrounds, and cultures.
Ultimately, fraud happens when we have a lapse of discernment of what's true and what's fake.
So one specific Behavior Design Fogg Maxim that Kreitzberg and Ngo applied is to "Help people Feel Successful." In addition to helping people feel successful, Kreitzberg and Ngo attribute their success to incessant discipline to return to the“SnapTesting” process week after week. SnapTesting is a specific Behavior Design method in which you test the psychology behind your idea in four hours of work or less. You quickly learn if you’re designing for the right behavior or if you should drop it and move onto another behavior. Do it over and over again and meaningful insights cannot be denied if "failures" are integrated into learnings as fuel for the next SnapTest.
In month 1, Kreitzberg and Ngo started off SnapTesting v1 of the intervention with motivated friends and family. Their intent was to 1) see if this cohort would do the target behavior and 2) iron out any wrinkles in the process. This was a low-risk method of testing the idea before SnapTesting with higher risk scenarios: actual businesses and their employees.
As anticipated, Kreitzberg and Ngo started SnapTesting the improved v2 of the intervention with small businesses in month 2. New insights were uncovered, setbacks overcome, and ultimately meaningful behavior change was unlocked over the next two months By Month 4, they had a clear process for the intervention and the confidence to reach out to Margarita from the Peace Innovation Lab with their 68% increase of phish detection and a decrease to 0% of employees clicking on phishing links. After Margarita’s encouragement, they began to replicate their results and invest in engineering a scalable solution with the specificity supplied by the iterate SnapTests.
More work needs to be done, but the real-world cases and the PeaceTech, prosocial behaviors facilitated by Kreitzberg’s Designed Privacy program seem promising, especially with a closing statement by the Lab’s co-director, Margarita Quihuis:
“I think the power in what you’ve done is that it’s a first step in a behavior chain to enhance people’s critical thinking skills. As provocateurs fill the internet with clickbait, fake news, fake books (see Amazon) and fake information, it’s getting harder and harder for people to discern what’s real and what’s not. Almost all of us have been touched by fake emails and phishing scams. The personal, political and social repercussions are clear – erosion of trust, bad data and erroneous conclusions on what to do on pressing social issues. Can we baby step people forward to sharpen their critical thinking skills to protect themselves from malicious manipulation? A small skill like discerning email phishing schemes could be the vital first step.”
You can reach David Ngo, Behavior Designer in Residence at the Lab at: david@peaceinnovation.com
Click here to learn more about Designed Privacy.
Click here to learn more about Behavior Design: SnapTesting.
Click here to try a part of the Behavior Designed Cyber Awareness program designed by Kreitzberg and Ngo.